|
Restricting Access |
|
The Security Manager provides the option to restrict or allow access to specific objects (i.e. screens, panel controls, queries, query columns, data dictionary, data elements, views, reports) only for selected security classifications. Only users in the selected classification(s) are allowed access. For example, a panel control will not display to users who are not in the assigned classification.
By default, if no security classifications are assigned, there is no security and all users are granted full access.
For information on the various locations where security can be applied, see Applying Object Security.
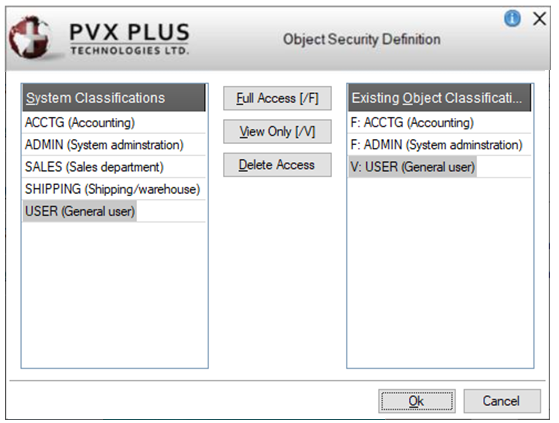
Object Security Definition is used to apply security to a specific object by only selecting security classifications that are allowed either full access or view only access to that object. Doing this allows only users in the selected classifications to have access, as specified.
If you do not want certain security classifications to have either full or view only access, then those classifications should not be selected. In that case, users in the omitted classifications will not be allowed either full or view only access.
This window consists of the following:
|
System Classifications |
Lists all security classifications currently defined in the system, including the two default classifications, ADMIN (for system administration) and USER (for general users). |
|
Existing Object Classifications |
Lists the names/descriptions of selected security classifications, prefixed with either F (full access) or V (view only). This list box is initially blank, which indicates all users have full access. Select a classification in the System Classifications list. Then click either the Full Access [/F} or View Only [/V] option. The selected classification is added to the Existing Object Classifications list, prefixed with either F or V. Multiple classifications may be added, one at a time. |
|
Full Access [/F] |
Button used to apply full (ADMIN) access to the selected security classification. |
|
View Only [/V] |
Button used to apply view only access to the selected security classification. |
|
Delete Access |
Button used to delete a selected classification from the Existing Object Classifications list. Users in the deleted classification will no longer be allowed to access the object. The classification is deleted from this list. It is not deleted from the NOMADS security classification file. |
|
OK |
Saves the changes and closes the Object Security Definition window. |
|
Cancel |
Closes the Object Security Definition window without saving any changes. |
Object Security Definition can be invoked from various locations when defining the following:
|
Location |
Method | ||||||||||||||
|
Panel Header |
Click the Security button at the bottom of the Panel Definition window. | ||||||||||||||
|
Control Properties |
Click the Security button at the bottom of the Properties window for the following panel controls: | ||||||||||||||
|
Data Dictionary |
Select Utilities > Security from the menu bar in Data Dictionary Maintenance. | ||||||||||||||
|
Data Element |
Click the Security button at the bottom of the Element Description window. | ||||||||||||||
|
Data Source |
Click the Security button at the bottom of the Update a Data Source window when editing an existing data source definition. See Data Source Maintenance. | ||||||||||||||
|
View |
Click the Security tool bar button in the Define a View window. | ||||||||||||||
|
Standard Query |
Click the Security tool bar button in Query Definition and in Query List Definition. See Query Security. | ||||||||||||||
|
Query Column |
Click the Security button at the bottom of the Column Options window when editing a selected query column. See Query Security. | ||||||||||||||
|
Query Formula |
Click the Security button at the bottom of the Query Formula Definition window. See Query Security. | ||||||||||||||
|
Query File Link |
Click the dotted button in the Security grid column in Query File Link. See Query Security. | ||||||||||||||
|
Report |
Select File > Restrict Access from the menu bar in Report Designer. | ||||||||||||||
|
Customizer |
Click the Security button at the bottom of the Define File Item window when defining a user file item (field). See Customizer Security Considerations. |
Because it is possible to restrict or allow access to the different levels, a hierarchy is in place that establishes which level of security takes precedence over the other. For example, a user whose security classification does not have access to the folder but has full access to a sub-panel of that folder will find the entire folder is hidden. As a result, this user is unable to access the tab for the sub-panel to which access had been granted.
Example:
The following examples show the result of the level hierarchy when access is restricted or allowed at different levels:
|
Example 1 |
Result |
|
Full access to the panel is allowed. |
Access to the panel is allowed, and the individual control is hidden. |
|
Example 2 |
Result |
|
Full access to the sub-panel is allowed. |
Entire folder is hidden; as a result, there is no access to the tab associated to the sub-panel. |
|
Example 3 |
Result |
|
No access to the sub-panel. |
Access to the folder is allowed, and the tab (associated to the sub-panel with no access) is hidden. Other tabs on the folder are shown and can be accessed (if full access was granted). |
|
Example 4 |
Result |
|
View only access to the panel is allowed. |
All individual controls on the panel are disabled. |
Folder controls can be defined to display tabs, which are associated with previously created sub-panels. The tab information for each sub-panel is defined in the Tabs Definition grid within the Tabs/Folders dialogue. For information on adding, removing or modifying the sub-panels in folder controls, see Adding and Modifying Sub-Panels.
You can view the Security column in the Tabs Definition grid to determine if any security had been previously applied for each of the sub-panels within the selected folder. If security has been applied, the Security column displays the classification name preceded with either F (Full Access) or V (View Only).
Example:
In this example, the Security column indicates that security was previously applied to the "Invoices" and "Payments" sub-panels but not to the "Address" sub-panel.